- Passwords should consist of a minimum of EIGHT characters to a maximum of THIRTY characters.
- Password complexity should be a combination of alphanumerical, at least one upper case, at least one lower case character, and at least one special character.
- Password should contain at least one numerical value (e.g. 0-9)
- Password should contain at least one each of upper and lower case characters (e.g., az, A-Z)
- Password should contain at least one special character (e.g. !@#$%^&*()+=)
- The system should not allow reusing the last 3 passwords.
- The system should not allow using the user’s first and or last name used in the system.
- The system should not allow using a username, email id, or phone no. used in the system.
- Password should not be allowed to contain a sequence of repeated characters e.g. aaa123 is an invalid password
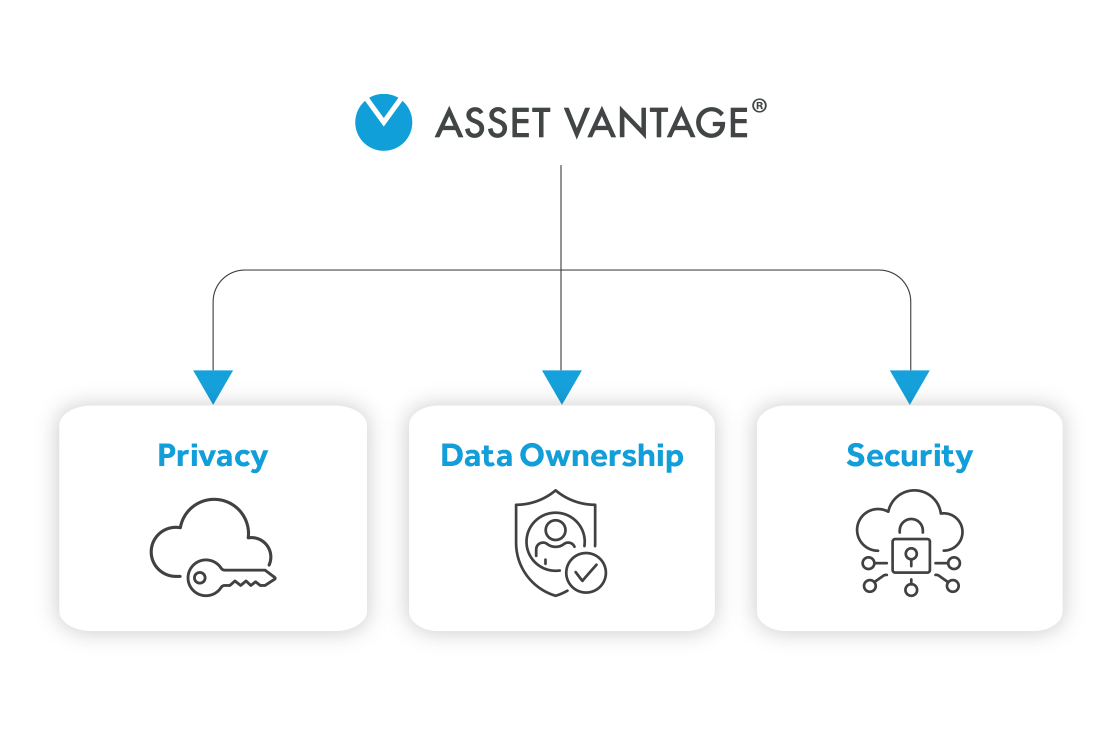
The AV platform is built on a foundation of total data privacy and best-in-class security allowing auto-back up with full ownership of your own data.
State of the art encrypted data hosting & networking
We use Amazon Web Services (AWS) exclusively for our entire application stack.
AWS is SSAE16 SOC1/SOC2/SOC3 certified & GDPR compliant.
Your data is always encrypted in-transit using TLS and at rest using AES-256 based encryption at the database level.
24×7 threat assessment and monitoring
We offer 24×7 live monitoring of client URLs using our partners for ongoing web security and safety to keep ahead of the security curve.
Comprehensive user role management & audit trail
AV features user roles and permissions for access control with an audit trail to keep a track of all data activity by user session.
Clients have the option of using Dual Factor Authentication for login using the AV mobile app.
Choose where your data lives
Clients have the option of selecting their own data center from AWS global regions.
Dedicated & Custom URL
Each client system is configured as a unique URL and with a database instance that can be setup for access through a VPN.
